Ransomware help guide
Discovering you may be the victim of ransomware
Typically, victims of ransomware become aware of an issue when they encounter a message stating that their system is infected and a payment is required to receive the decryption key. Prior to this message, they might have noticed unusual behavior on their machine, such as files failing to open or unexpected actions occurring.
If you suspect you’re a victim of ransomware, we’ve prepared a comprehensive list of steps for you to follow. We offer two guides: one tailored for businesses and another for individuals.
My Buisness has been hit by ransomware
Businesses typically suspect a ransomware attack when one of the following occurs:
- A user reports an infection on their machine or a server.
- A server or business application suddenly stops functioning.
- The IT Security team detects ransomware-related activity on business systems.
- An attacker privately informs the business of a breach, or announces it publicly on a forum or social media.
All these indicators should be taken extremely seriously. While they may sometimes be false alarms, they can also be early signs of a significant issue.
For businesses operating under EU law, any suspicion of ransomware must be promptly investigated, as you are required to report the breach to your country’s Data Protection Commissioner within 72 hours. You can report a breach to the Data Protection Office in Ireland here.
A swift initial incident response investigation is crucial to scope the scale of the breach and put measures in place to prevent it spreading. It could also reveal the ‘breach’ to be a false alarm or, quite commonly, a scareware that mimics ransomware. In such cases, there would be no need to report a breach to the DPO and the incident response would be simpler.
Remediation process
- Upon identification of ransomware, initiate an Incident Response immediately. Your IT team should document the specific type of ransomware and ensure it is confined to the endpoints where it was detected. If your business lacks an IT team, capture images of the ransom message and power down any infected devices.
- The Incident Response team should build a timeline that traces how the devices were infected. Upon identification of the attack vector, they should implement controls to prevent further infections.
- At this point, your IT team and business are presented with a decision. The devices infected by ransomware can be reset to eliminate any traces of the malware. However, this may not always be feasible and could lead to data loss if backups were not maintained. The business might opt to pay the ransom in the hope of receiving the decryption key.
Cryptie can assist businesses in circumventing the complexities associated with acquiring a substantial amount of cryptocurrency. Businesses can conduct a standard bank transaction with Cryptie, and we will manage the more challenging cryptocurrency transaction for you. If you require this service, please reach out to us using our secure contact form.
My personal machine is infected
If you suspect you’ve fallen victim to ransomware, you should use another device, such as a phone, to take clear photos of the messages appearing on the infected machine’s screen. Make sure the images are legible. Try to gather an idea about how the infection occurred, for instance, did you download anything recently? Note down any strange activity you encountered before or when you spotted the suspected ransomware. If you’re unsure about handling this situation on your own, the pictures and other details can be forwarded to the person assisting you.
IMPORTANT: Avoid calling numbers found online for computer assistance and refrain from using tech support that are asking you to download software like Anydesk or TeamViewer for remote problem-solving. Most of these are technical support scams originating from overseas. Be aware that scammers may use Google ads to appear as the top result when you search for technical help in your area.
Once you’ve captured images of the suspected ransomware, switch off your machine to prevent more files from being encrypted.
Investigate the malware
In some instances, individuals who suspect they have ransomware are actually encountering messages from another type of malware known as scareware. Scareware can appear in emails, pop-ups, or on websites, and it attempts to convince you that your machine is infected. Following the instructions of scareware can ironically lead to an actual ransomware infection. Therefore, it’s crucial to quickly determine whether your files have actually been encrypted or if you’re simply being misled into thinking they have. Below are a few pictures showing real scareware examples.
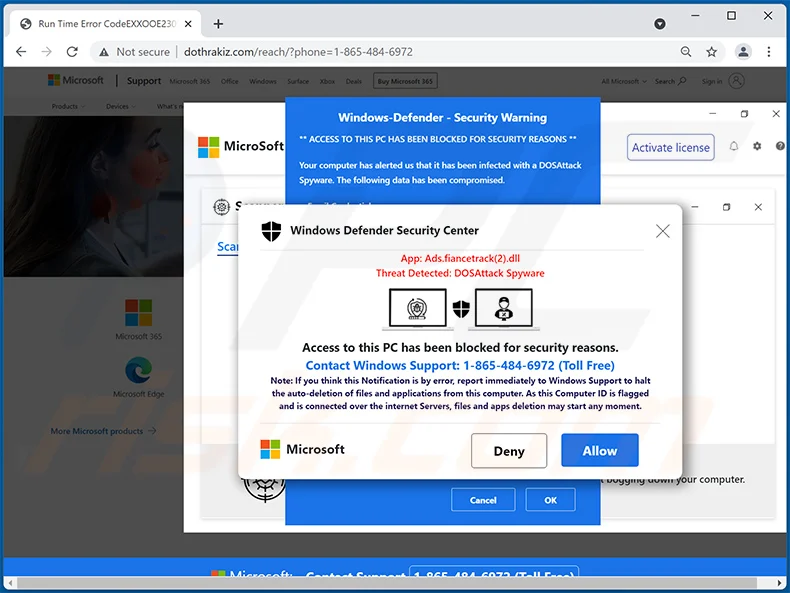
Scareware often appears on websites, attempting to mimic system pop-ups. However, these are not genuine system alerts and are entirely confined to the website you’re visiting.
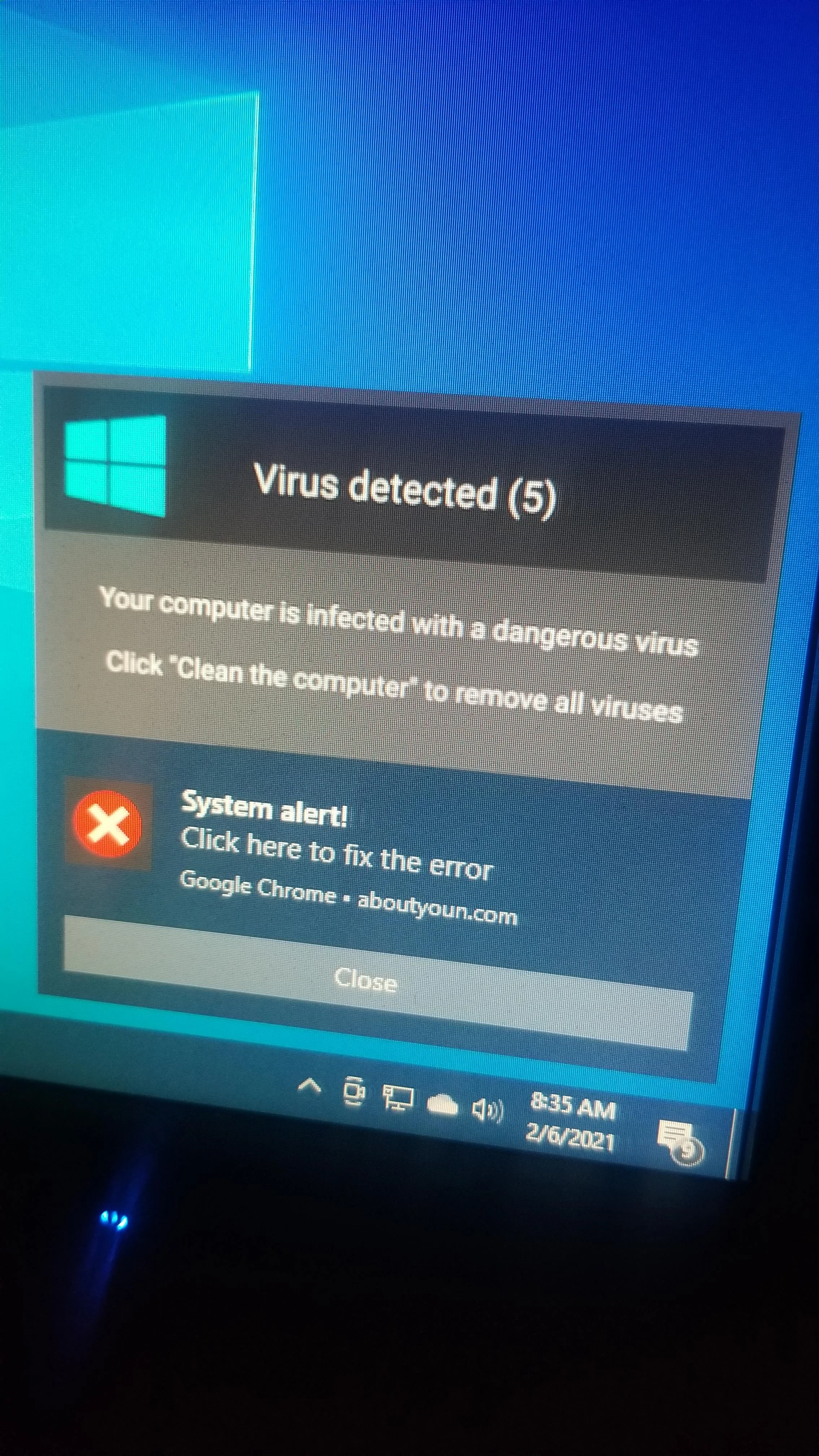
A prevalent type of scareware involves websites requesting alert permissions in your browser. These sites then send alerts intended to convince you that your machine is infected. To address this, remove all site permissions in your browser and clear your cache.
Indicators that the ransomware is not real:
- If the ransom message is only within a website, it is not real.
- If the ransom message appears as a notification in the bottom right of your Windows desktop, it is not real.
- If the ransomware appears in an email, it is generally not real.
- If you're made aware of ransomware while interacting with technical support you found online, you are likely being scammed.
Indicators that the ransomware is real:
- An application window appears on your desktop with the ransom message. If you open your computer's file explorer, your file names or their extensions are now different.
- Your PC has become unusable and the only thing that appears is a ransom message.
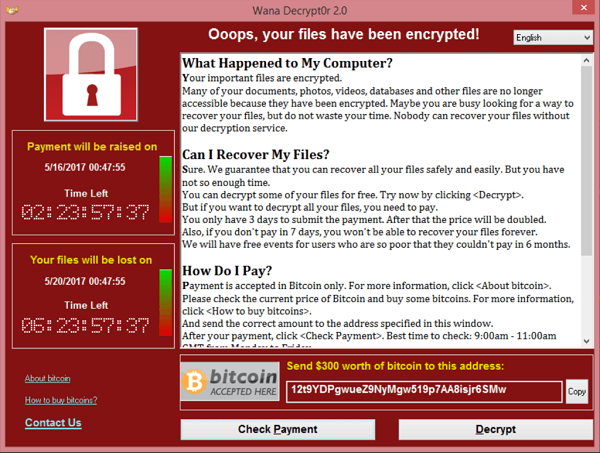
Real example of the WannaCry ransomware.
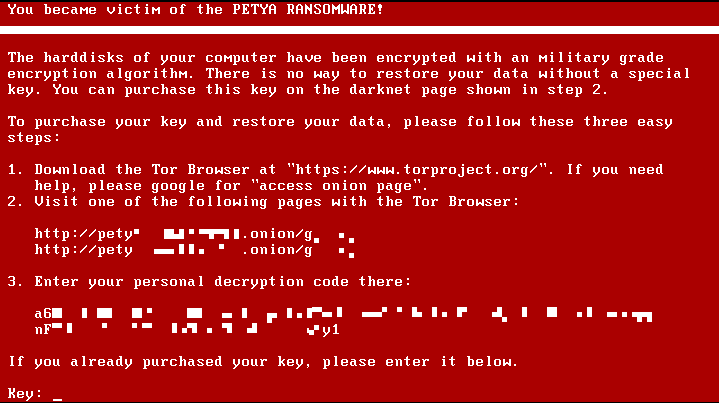
Real example of the PETYA ransomware.
Fixing ransomware
If you’ve confirmed that your machine is indeed infected with ransomware, refrain from turning it back on. This precaution is to prevent further encryption of your files. In extreme cases, some computer repair shops may be able to manually recover any files that the ransomware has not yet encrypted.
Once your computer files have been encrypted, they become extremely difficult to decrypt without the key. While some older ransomware variants may have their encryption keys exposed online, enabling data recovery, ransomware is continuously evolving and becoming more sophisticated. Newer versions are unlikely to be cracked as easily.
Unfortunately, decrypting ransomware without paying the ransom is exceedingly challenging and unlikely to succeed, even with the assistance of IT security professionals.
With this considered, we recomend you follow the below steps to come to a resolution.
- Stay calm, understand the perpetrators are more interested in money than in harming you. Do not let this stressful situation affect your health.
- Ransomers are use to waiting days or weeks for payment, do not feel like you need to fix the issue on the day it happens.
- Assess the data that you stand to lose if your files cannot be recovered. Are you able to accept the loss of this data? If so, we recommend performing a factory reset on your device to remove the ransomware.
In cases where you'd prefer to pay the ransom, Cryptie makes this as easy as possible for you. You can contact us using this contact form. However, it’s important to note that there’s a possibility that the ransomers may never return the key. Cryptie will evaluate your specific ransomware case and provide an estimated probability of a successful outcome if you pay the ransom.